Days off for you are days on for cyber attackers. While workers take their well-deserved vacations, cybercriminals are lurking, ready to take advantage. Organizations new to having employees work remotely find themselves facing a similar risk. Those without in-house security teams could leave their organization vulnerable and needing to know steps to prevent cyberattacks. Without the means to properly detect sophisticated cyberattacks on their systems, networks, and devices, they could be left to fester instead of containing the threat before damage is done.
Attacks Uptick as People Are Away
Holidays and extended weekends are an open invitation for cyber attackers to penetrate large and small organizations’ defenses. The SolarWinds 2020 attack fell right around the Christmas holiday season and targeted the software of MSPs and their customers, one of the first examples of third-party risk transfer. JBS Foods was the target of a massive breach on Memorial Day 2021 (paying the equivalent of $11 million in ransom), and the Colonial Pipeline critical infrastructure ransomware attack centering on Operational Technology occurred around Mother’s Day 2021.
Cybersecurity breaches often occur when we’ve let our guards down or have other activities in mind. Cyber attackers are always working, taking advantage of that vulnerable time window.
A Critical Time for Cybersecurity Breaches
In addition to being more relaxed and perhaps not as diligent regarding cyber safety and protocols, other factors are at play during common travel seasons or organizations new to working from home. Lack of resources or IT help is often exacerbated, with key staff taking a vacation and working remotely. That’s in addition to the already thin labor force characterizing the IT market. The number of U.S. job openings for the software and IT industry has grown 119% since the pandemic, so experienced cybersecurity technicians are in demand.
Ransomware and other cyber-attacks can take time to spread through the network, so the longer it takes to detect and respond, the more potential for damage. Overworked IT staff may need to handle more alerts per person, increasing the chance of an attack going unnoticed. Organizations without a dedicated security team may not be aware of any compromise until they’ve returned to work—letting ransomware demands increase exponentially.
It’s the perfect storm for a cyber-attack. Other heightened data breach risk factors may include social engineering from out-of-office replies, sharing personal posts that can be used for attacks, completing personal work on company-owned devices, and scam emails and SMS messages that open the network to vulnerability and takeover.
Data Breaches Magnify
Data breaches can take many different forms, but essentially, they are various types of access to sensitive, confidential, or unprotected information. These can include:
- Unauthorized access refers to a threat actor infiltrating the systems, an accidental data leak, an insider threat, or anyone who does not have the authority to access or possess that information.
- Different types of unauthorized access encompass viewing information, such as a medical file that you do not have access to (still unauthorized even if it’s not disseminated), as well as copies of documents, transmissions, and stolen information.
Luckily, managed detection and response technology means even non-enterprise companies with limited resources can proactively and immediately uncover cyber threats.
What is Managed Detection and Response?
Managed detection and response is a crucial part of every business cybersecurity process. With a robust managed detection and response solution, organizations of every size can immediately identify potential threats to their network, systems, and devices and quickly stop the attack.
Cyber-attacks can occur at any moment, so you need a 24/7 cyber alarm system to identify, alert and stop cyber threats.
Managed detection and response is automated, utilizing artificial intelligence to consistently scan for malicious activity across all device endpoints, systems, and networks. An external cybersecurity service monitors activity around the clock, and in the case of a detected incident, quickly acts to prevent its spread. It provides key stakeholders with updated reports on the state of their cyber-hygiene, any suspicious behavior or vulnerabilities found, and recommends areas for improvement.
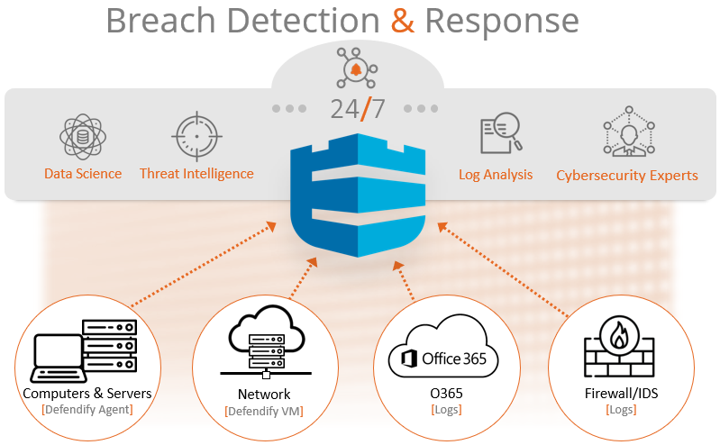
Managed detection and response significantly reduces the risk of operational downtime and potential loss of business by rapidly addressing active cyber incidents, consistently monitoring for vulnerabilities, and strengthening the overall cybersecurity posture.
Why is Managed Detection and Response Important?
The best way to avoid loss from a data security breach is to prevent it from happening with rapid, automated detection. Other services operate like breach detection and response, but under other names.
Other Cybersecurity Protection
- Endpoint Detection and Response (EDR) focuses solely on the endpoint, neglecting cloud applications, network activity, and perimeter security. It obtains and analyzes security threat data from computer workstations and other endpoints.
- Security Information and Event Management (SIEM) collects data from different sources. Think of this as the technology piece that gathers all the information, sorts through it, and produces alerts. Its core capabilities are a broad scope of log event collection and management and the ability to analyze events across multiple sources and operations. While it collects automatically, IT resources must manually review alerts and conduct a subsequent investigation.
- Security Operations Center (SOC) is the facility and team that reviews the alerts or network activity that might be suspicious. Generally, their job is to supervise the site or network and provide recommendations to IT for response and remediation.
- Extended Detection and Response (XDR) is one of the latest emerging tools in the arsenal of breach detection and response. This intelligent alerting system automatically collects and correlates data across multiple security layers and all corporate endpoints.
The Importance of Layered Protection
Travel seasons or times where many would be out-of-office are the go-time for cybercriminals or state actors. However, with a robust managed detection and response system combined with assessment and testing, training and policies, you can significantly strengthen your cybersecurity defenses.
Active threat detection and response is essential, and you don’t need an in-house team to make it happen. Defendify’s managed detection and response module includes everything you need to identify the latest threats, including cloud and email coverage. Our vigilant and dedicated solution, backed by our team of security experts, is on your side, providing actual response.
More Managed Detection and Response Resources:
Webinar: Why Cyberattacks Aren’t Just for the Enterprise, and What To Do About It
Webinar: Cyber Insider: MSP Stories From The Trenches
Blog: No Security Team? No problem!
Resources & insights

Why You Could Be Denied Cyberattack Insurance Coverage

Cost of a Cyberattack vs. Cybersecurity Investment

Defendify Listed as a High Performer in Six G2 Grid Categories

Why You Could Be Denied Cyberattack Insurance Coverage

Cost of a Cyberattack vs. Cybersecurity Investment

Defendify Listed as a High Performer in Six G2 Grid Categories
Protect and defend with multiple layers of cybersecurity
Defend your business with All-In-One Cybersecurity®.
Explore layered
security
Learn more about Defendify’s three key layers and All-In-One Cybersecurity®.
How can we help?
Schedule time to talk to a cybersecurity expert to discuss your needs.
See how it works
See how Defendify’s platform, modules, and expertise work to improve security posture.







