What is Spear Phishing in Social Engineering?
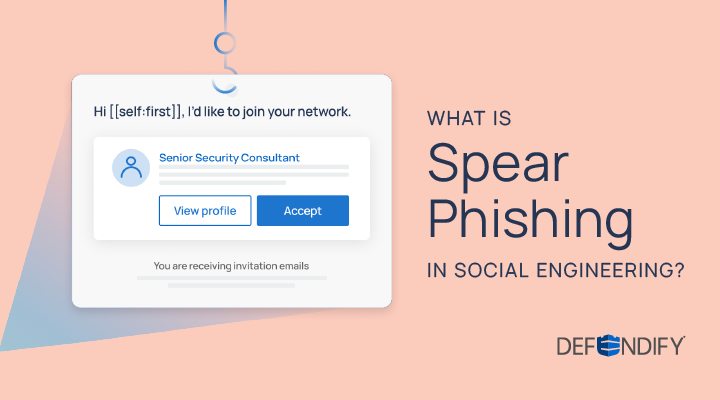

Phishing attacks look different than they did in the past; they are more sophisticated, calculated, and difficult to identify. Staying vigilant and training your employees to respond to cyberattacks can safeguard your organization against the damages caused by social engineering schemes.
At the most basic level, phishing manipulates people into giving out personal data or clicking on a malicious link, often through email, SMS (smishing), or phone calls (vishing).
When email was first popular, phishing attacks were almost comical in their approaches. Many of us have probably received the infamous, money-demanding email from a Nigerian prince or a fake plea from a distant relative who’s “stranded in a faraway country and needs help immediately”. While these schemes are easy to identify and sometimes downright ridiculous, other forms of phishing aren’t nearly as easy to spot. Spear phishing in social engineering is an example of a more sophisticated approach, in which a bad actor takes a deep look into the target’s background and relies heavily on human psychology to create a sense of urgency and fear.
Spear Phishing Versus Phishing
Typically, people find regular phishing attacks easy to identify because they’re so generic. For example, a phishing attack might send out a mass email, spoofing a specific bank and requesting that the recipient enter their personal information into a malicious website disguised as the bank’s login page. However, what if the target isn’t actually a member of this bank, or if they just checked their account earlier that day and know the claims are false? In these cases, it’s fairly easy to tell that this email isn’t legitimate.
On the other hand, spear phishing in social engineering is more specific than “regular” phishing. Instead of sending out a generic mass email to a group of people, the attackers behind this form of social engineering target specific individuals. This type of attack is more complex as they are tailored to their individual target’s lifestyles, fears, and vulnerabilities. Contrary to “regular” phishing, attackers use publicly available information or data collected from previous breaches and sold on the black market to find specific, accurate information about their victims.
When it comes to attacks within corporations, threat actors attempting a spear phishing attack might leverage information such as:
● Details on executive and high-level employees
● Employees in finance/payroll, notable company events, projects, or news
● Notices of new employees
● Customers, vendors, or partners of the organization
● Out-of-office notifications or personal social media posts about senior leadership being away
Types of Spear Phishing in Social Engineering Techniques
There are a few specific techniques that attackers will use when targeting individuals within a business:
Clone phishing
Clone phishing means attackers clone a familiar brand’s email address, then send a request to either click on a link or fill in sensitive information. When it comes to attacking corporations, malicious actors often choose to clone software tools that companies use daily, such as Microsoft, Slack, or Zoom. They also work hard to copy the format and branding followed by these corporations. Because employees are already comfortable using these tools regularly, they often don’t look closely at these emails and either click on the malicious link or fill in their information without hesitation.
In addition, attackers include standard calls to action in these cloned emails, such as requesting users to change their passwords or verify their account credentials. Employees tend to fall for clone phishing emails because they ask for something that isn’t out of the ordinary.
Targeting new employees
New employees can be particularly vulnerable to spear phishing for a few reasons. For one, new hires must send sensitive information such as tax forms and their social security number upon getting hired, which allows attackers to spoof the HR department and request this information.
In addition, new employees tend of be eager to please, on top of not yet having learned the communication methods and styles of each of their new colleagues. As a result, they’re much more likely to fall for clone phishing attempts that look like they’re coming from a manager or co-worker.
Senior leadership team spoofs
Spear phishing attackers also use the email addresses of the senior leadership team to create urgency and send requests that look legitimate; this scheme is also called Business Email Compromise. The attacker poses as a senior leadership member, then requests a wire transfer or other compromising action from an employee. CEO fraud especially works well on employees because of their desire to be helpful and do a good job in addition to the pressure of receiving a request from such a high-up authority figure.
What Is Whaling?
Whaling falls under spear phishing in social engineering but specifically targets executives. The attackers do extensive research and preparation, then reach out to a C-level employee specifically, often hoping to gain access to financial or payroll information.
Because leadership information is usually visible to the public on company websites, a malicious attacker can easily find out the names of an executive’s trusted colleagues, then use spoofing or stolen credentials to send an email to this target. Whaling schemes go after lucrative, high-profile figures- some even targeting celebrities or politicians.
Best Practices for Preventing Spear Phishing
Fortunately, there are a few ways to prevent spear phishing within your organization:
- Training
First and foremost, organizations must train employees to spot phishing and spear phishing emails. Training courses for new hires and annual refreshers make a huge difference. In addition, training reinforcement is necessary, such as monthly microlessons or other types of ongoing reminders.
- Phishing simulations for employee practice
Next, employees need to practice spotting phishing emails using realistic examples.
Phishing simulations enable this type of learning by sending unannounced fake phishing emails to employees. These simulations keep the possibility of phishing emails top-of mind for employees, and also allows for further education for anyone who takes the bait.
- Technology tools
Spam filters and other fraud prevention tools can prevent employees from even seeing phishing emails in the first place. These solutions could include Domain-based Message Authentication Reporting and Conformance (DMARC), DomainKeys Identified Mail (DKIM), Sender Policy Framework (SPF), and Multi-Factor Authentication (MFA).
Although spear phishing may be more challenging for employees to identify than regular phishing, there are still ways to avoid falling for these schemes. Educating your teams, giving them opportunities to practice their skills, and installing technology solutions can all help to strengthen your cybersecurity posture. As a bonus, your employees will use security awareness in the workplace and pass what they learned along to family and friends.
TL; DR
- Spear phishing in social engineering is more specific and targeted than “regular” phishing.
- Cybercriminals use publicly available information collected from data breaches and sold on the black market to find accurate information about their victim.
- The most common spear phishing techniques are clone phishing, the targeting of new employees, spoofs from senior leadership, and whaling.
- Organizations should use ongoing cybersecurity training and technology to combat sophisticated spear phishing attempts.
Resources & insights
The Ultimate Guide to Phishing & Social Engineering

How to Spot a Phish: Tips to Spoil Advanced Phishing Attempts

The Ultimate Guide to Phishing & Social Engineering

How to Spot a Phish: Tips to Spoil Advanced Phishing Attempts
Protect and defend with multiple layers of cybersecurity
Defend your business with All-In-One Cybersecurity®.
Explore layered
security
Learn more about Defendify’s three key layers and All-In-One Cybersecurity®.
How can we help?
Schedule time to talk to a cybersecurity expert to discuss your needs.
See how it works
See how Defendify’s platform, modules, and expertise work to improve security posture.







